Businesses today require an increasing level of integration with third-party vendors, clients, and partners. Intertwined ecosystems increase vulnerability, severity of impacts and frequency of a disruption from a cyber attack. To meet this challenge, Cyber Tygr offers the Healthcare Security Program, a combination of security services inspired by best practices and regulatory compliance requirements.
Contact Us
When healthcare executives set reasonable, incremental goals and demonstrate a willingness to try new training methods, creating a culture of cyber awareness may be achieved. Given the volatility and increasing sophistication of the threat landscape, it is imperative.
We imitate a sophisticated phishing attack to test your employees, follow up with training to keep your company’s vulnerabilities from being exploited, then deliver a report that details the organization’s performance showing you who clicked or downloaded on what, and when, and on which device.
Our vulnerability assessment uncovers vulnerabilities in the network and recommends the appropriate mitigation or remediation to reduce or remove the risks.
The assessment provides detail on patch management, account maintenance, and systems configuration with recommendations on how to mitigate discovered vulnerabilities. Our comprehensive reports include results of the vulnerability scans revealing vulnerabilities like old passwords, old patch levels, unnecessary services, FTP anonymous access, open e-mail relay, etc.
We monitor your infrastructure 24/7 and alert you to events that could be threats to the organization. Our Security Monitoring Solution includes the following capabilities: Click here to learn more
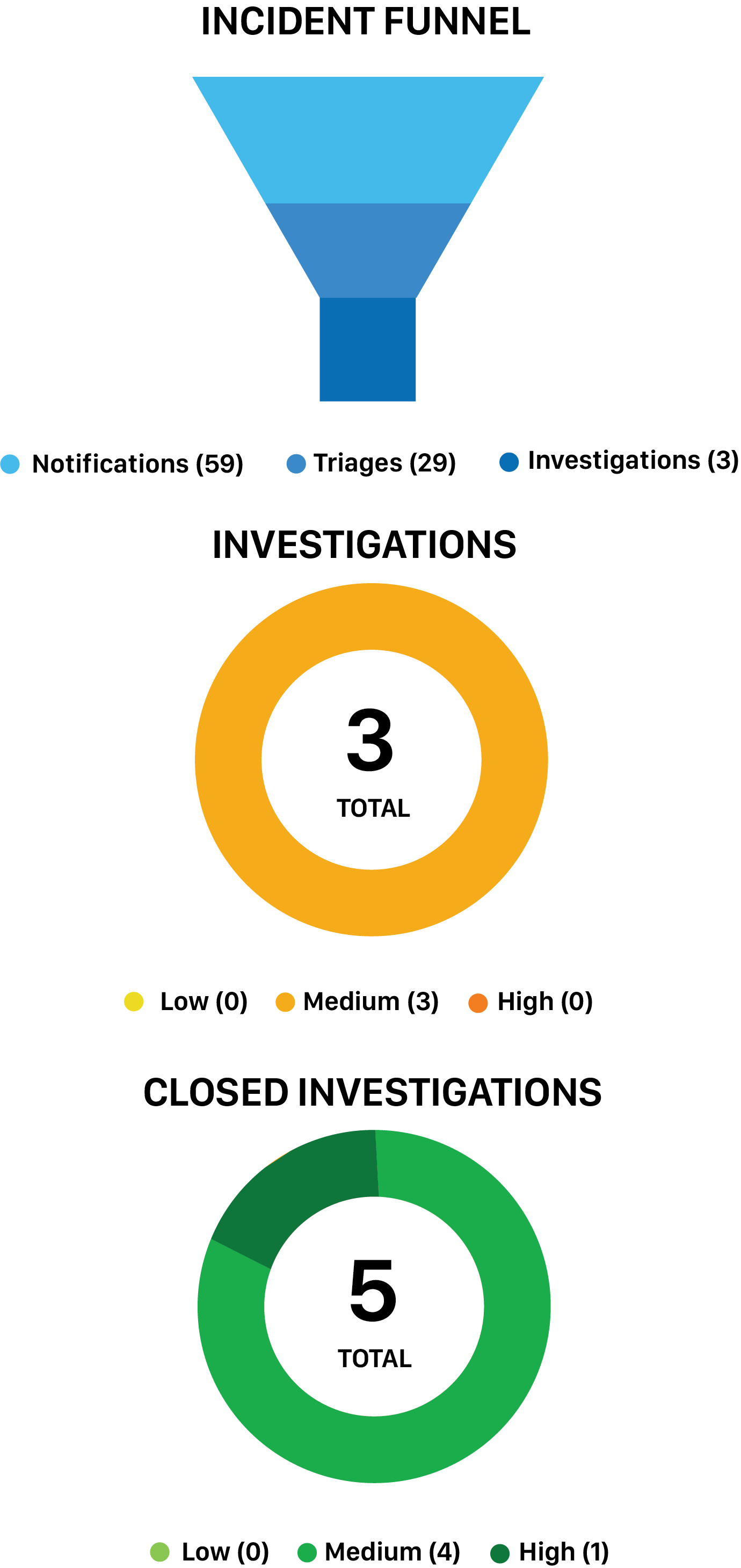
Security Operations Center & SIEM – User Reports and Dashboards sample

Services
Services
757-386-9725
info@cybertygr.com
4545 Commerce St. Suite 2004
Virginia Beach, VA 23462